
utilizes an Integrated Risk Management (IRM) approach that incorporates various risk management activities to protect its enterprise data assets from transaction, reputational, strategic, and compliance/legal risks. The risk management activities focus on the use, processing, storage, and transmission of data.
The risk management strategy utilized by Creighton University includes risk assessment, risk avoidance, and risk control.
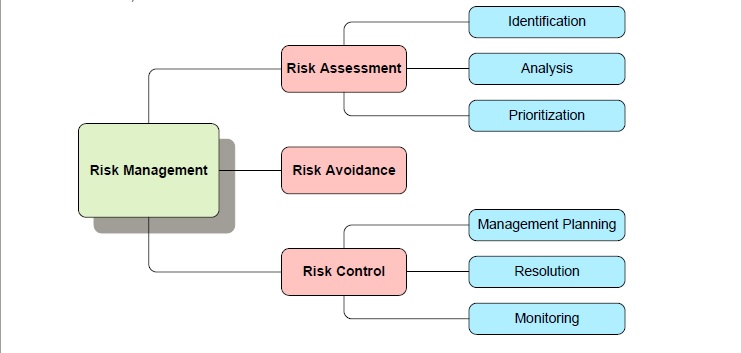
1) Risk Assessment
Risk Assessment includes at a minimum the following steps:
a) Identify the enterprise data assets and their potential security risks;
b) Analyze each identified security risk, and estimate the frequency and cost that would result from each occurrence (Single Loss Expectancy);
c) Quantify the Annualized Loss Expectancy (annual frequency x cost); and
d) Prioritize the analyzed risks and implement measures to avoid and control.
Based on Creighton University’s legal obligation to comply with certain federal and/or state mandated regulations, each data element (i.e. field) within the enterprise-wide data assets is "classified" by the appointed Data Steward as either:
Confidential (High Sensitivity)
Data should be classified as "Confidential" if its unauthorized disclosure could result in significant legal, financial, reputational, or other adverse impact upon the University, due to legal or regulatory requirements, University policies or agreements to which the University is a party, or because of the sensitivity of the information.
Private (Medium Sensitivity)
Data should be classified as "Private" when the unauthorized disclosure, alteration or destruction of that data could result in harm to the University’s image or reputation, or could undermine the confidentiality of University business or processes, but would not necessarily violate existing federal or local laws, University policies, or University contracts. Data in this category are not routinely distributed outside the University, and distributed within the University on a need-to-know basis.
Public (Low Sensitivity)
Data should be classified as "Public" when the unauthorized disclosure, alteration or destruction of that data would result in little or no risk to the University and its affiliates. Public data has no legal or other restrictions on access or usage and may be open to the University community and the general public.
Data elements classified as "confidential" or "private" are considered protected data and must be managed accordingly. Creighton’s list of protected data elements and their associated regulations can be found in the Risk Assessment Summary
2) Risk Avoidance
Creighton University has implemented a variety of preventive measures to reduce the probability of encountering potential security risks related to protected data:
a) Policies, Standards, Procedures, and Processes
Policies are living documents established by Data Governance that state in writing how the enterprise data assets will be protected by Creighton University, how auditing will be performed to identify any violations, and what actions will be taken when a violation is encountered. These policies will also include an "acceptable use" policy that outlines the plans to continually educate the end- user community about protecting the university’s enterprise data assets.
Standards are typically documents defined by the IT Data Custodians to ensure that industry "best practices" are being applied to enterprise data management in a consistent manner in product analysis, design, development, testing, configuration management, implementation, operations, training, and support.
Creighton’s policies and standards can be located in the Guide to Policies Document
Procedures provide a prescribed sequence of steps used to define "how to" perform self-servicing tasks associated with data management. Procedures can be located in the How-to-Guides
Processes are built and maintained by the IT Data Custodians to automate the monitoring and alerting on violations encountered against Data Governance policies and standards. Processes can be located in the Job Scheduling
b) Access Roles
Role-Based Access Control (RBAC) is the method used to control access to data assets based on the roles defined for individual users and/or groups within the enterprise. The access role authenticates and authorizes the user to certain entitlements based on job responsibilities, and the level of business/ technical competency. When implemented properly, RBAC enables users to perform a wide range of authorized tasks by dynamically regulating their actions according to reusable functions, relationships, and constraints. Access roles are located in the Access Role Summary
c) BI Tool Entitlements
Access roles are given certain BI Tool entitlements (i.e. rights) based on the access role. BI Tool entitlements are grouped into Access Levels (i.e. self- service levels), where an Access Level is assigned to an access role. BI Tool entitlements are located in the BI Tool Entitlement Summary
d) Data Access Views
Data Access Views are created to control the amount of data available to user’s based on their job responsibilities (i.e. Access Role). Data Access Views are located in the Data Access View Summary
3) Risk Control
Risk control takes the information acquired during risk assessment and produces a risk management plan to deal with each potential risk, including mitigation alternatives, contingency plans, owners, and resolution procedures and estimated timelines. Ongoing monitoring will be performed to ensure that Creighton’s risk management strategy is executed in the most efficient and effective manner possible. The Risk Management Plan is located in the Risk Management Plan Summary

 2500 California Plaza
2500 California Plaza



